Safeguarding Your Business: A Comprehensive Guide to Protecting Your Workplace from Cyber Attacks
Introduction
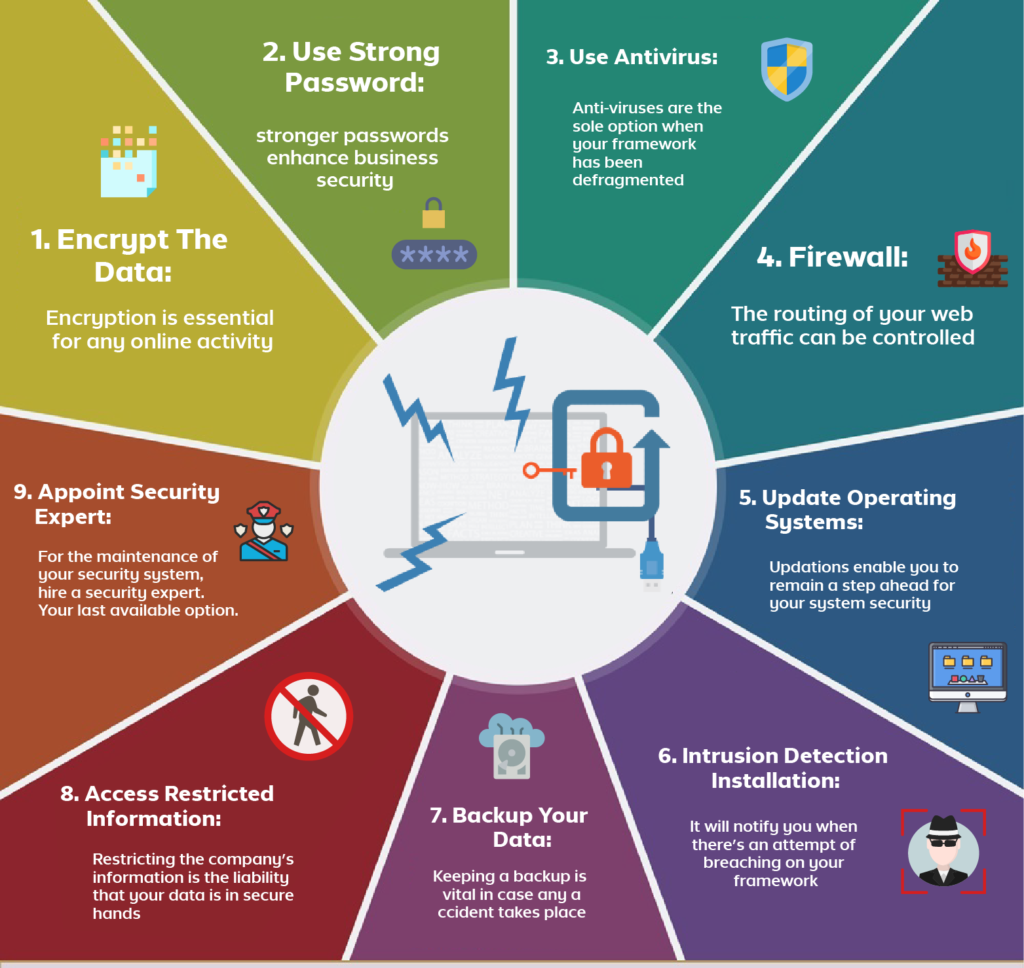
In the digital age, where businesses heavily rely on technology for their day-to-day operations, the threat of cyber attacks looms large. Protecting your workplace from these malicious activities is not only crucial for safeguarding sensitive data but also for ensuring the uninterrupted flow of business operations. In this blog, we will delve into the essential measures you can take to fortify your workplace against cyber threats.
Employee Education:
One of the weakest links in any cybersecurity defense is often human error. Conduct regular cybersecurity awareness training for your employees to educate them about the latest threats, phishing scams, and best practices for secure online behavior. Encourage the use of strong, unique passwords, and emphasize the importance of not clicking on suspicious links or downloading unknown attachments.
Implement Robust Authentication:
Ensure that your workplace implements strong authentication methods, such as multi-factor authentication (MFA). This adds an extra layer of security by requiring users to verify their identity through a combination of factors, such as passwords, biometrics, or security tokens. This makes it significantly harder for unauthorized individuals to gain access to sensitive systems and data.
Keep Software and Systems Updated:
Regularly update all software, including operating systems, antivirus programs, and other applications. Cybercriminals often exploit vulnerabilities in outdated software to gain access to systems. Automated updates and patches can help close these security gaps, reducing the risk of a successful cyber attack.
Firewall and Antivirus Solutions:
Implementing a robust firewall is essential for monitoring and controlling incoming and outgoing network traffic. Pair this with a reliable antivirus solution to detect and eliminate malware. Regularly update these security tools to ensure they are equipped to combat the latest threats.
Data Encryption:
Encrypt sensitive data to protect it from unauthorized access. This adds an additional layer of security, especially during data transmission. Implementing encryption protocols ensures that even if data is intercepted, it remains unreadable and unusable without the proper decryption key.
Regular Data Backups:
Create a routine backup schedule for critical data to mitigate the impact of a potential cyber attack. Backing up data regularly ensures that you can restore operations quickly in the event of data loss or a ransomware attack. Store backups in a secure, offsite location to prevent them from being compromised alongside the primary system.
Monitor Network Activity:
Implement network monitoring tools to keep a close eye on network traffic and detect any unusual patterns or activities. Early detection of anomalies can help prevent or minimize the damage caused by a cyber attack. Set up alerts for suspicious activities to enable a swift response.
Incident Response Plan:
evelop a comprehensive incident response plan outlining the steps to be taken in the event of a cyber attack. Assign specific roles and responsibilities, and conduct regular drills to ensure that your team is well-prepared to handle various scenarios. A prompt and well-coordinated response can mitigate the impact of an atta
Conclusion:
Protecting your workplace from cyber attacks is an ongoing process that requires vigilance, education, and the right technology. By implementing these proactive measures, you can significantly reduce the risk of falling victim to cyber threats and safeguard your business's sensitive information and operations. Stay informed, stay vigilant, and stay secure in the ever-evolving landscape of cybersecurity